
Git version control, aka Co-Authoring feature is AWESOME!
Co-authoring in canvas apps (experimental) - Power Apps | Microsoft Docs
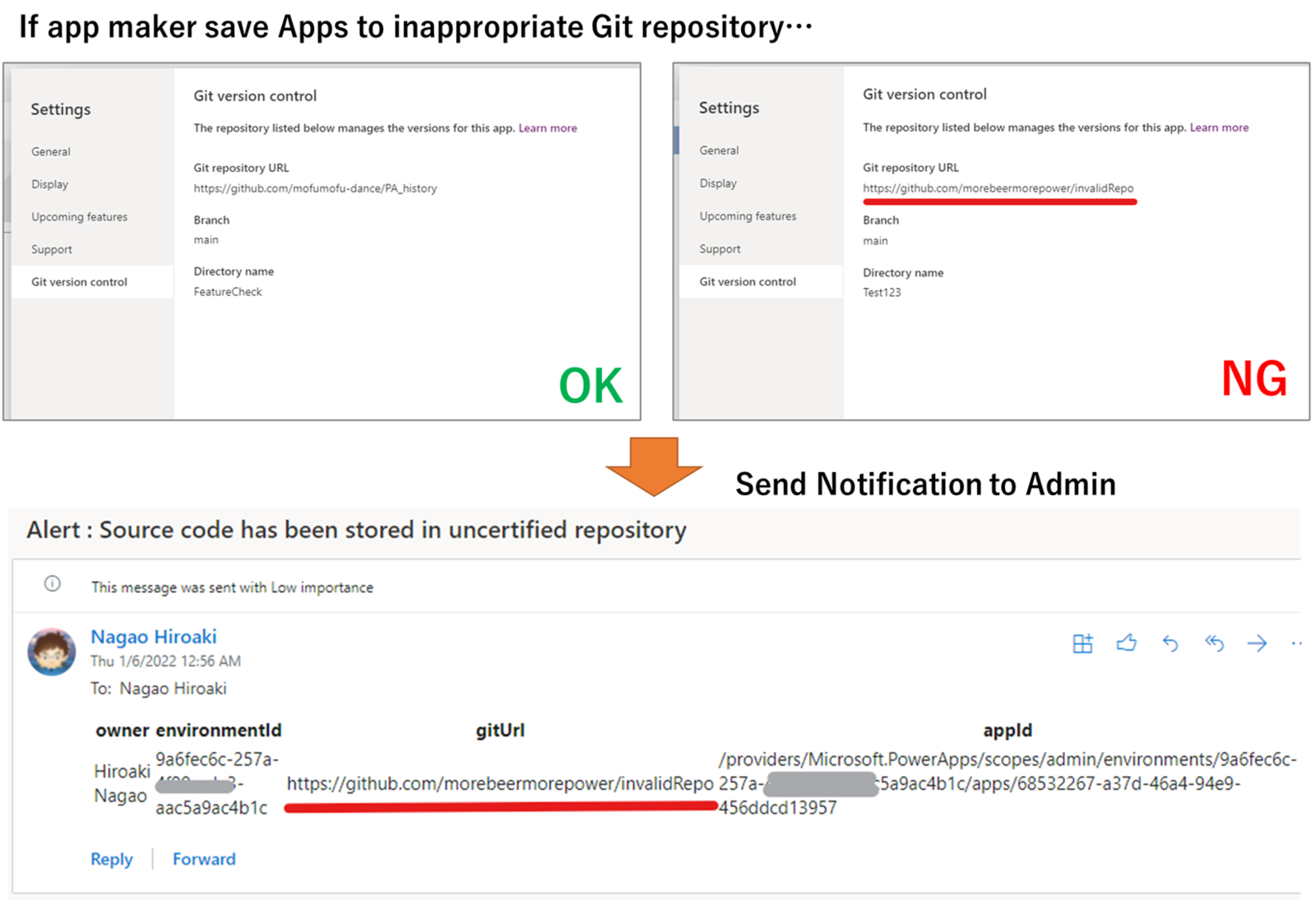
But... admins may be concerned that the source code may leak to inappropriate (= not managed by organization) repositories.
Actually, with the current CoAuthoring (experimental) feature, there is no check when setting up a Git repository, so makers can save their app code in any repository.
In this post, I would like to share the flow which detects inappropriate repository use and send notification to admin.
Use the "Power Apps for Admins" connector
With an addition of co-authoring feature, the Power Apps admin connector now returns information about the source control location (repository) as a property of the app.

In the flow, this property is used to notify the admin when the Git URL is other than the one specified by organization.
Set up Flow
The flow mainly consist of 4 parts of actions.
- List apps in each environment
- Filter apps which is enabled co-authoring feature
- Filter apps by comparing "sourceControl" property (Git Url) with one managed by organization
- If inappropriate app exits, send notification to admin

I will spare you the details, but in this way, you can use the information obtained from the Power Apps for admin connector to create a flow that periodically checks for storage in unauthorized repositories and notifies the administrator.
Sample flow
You can get above flow from my github repo ↓
Hope this will help admins :)